The safest and most efficient way to share and collaborate internally and between agencies
Fully secure collaboration, messaging and file sharing for government and law enforcement.
Zero Knowledge military grade encryption and security
Purpose-built for government and law enforcement
Bullet-proof protection for your files, messages & video conferences
How are you storing and sharing sensitive and confidential data internally and externally with other stakeholders or law enforcement partners?
4 red flags that put you at risk.
![]()
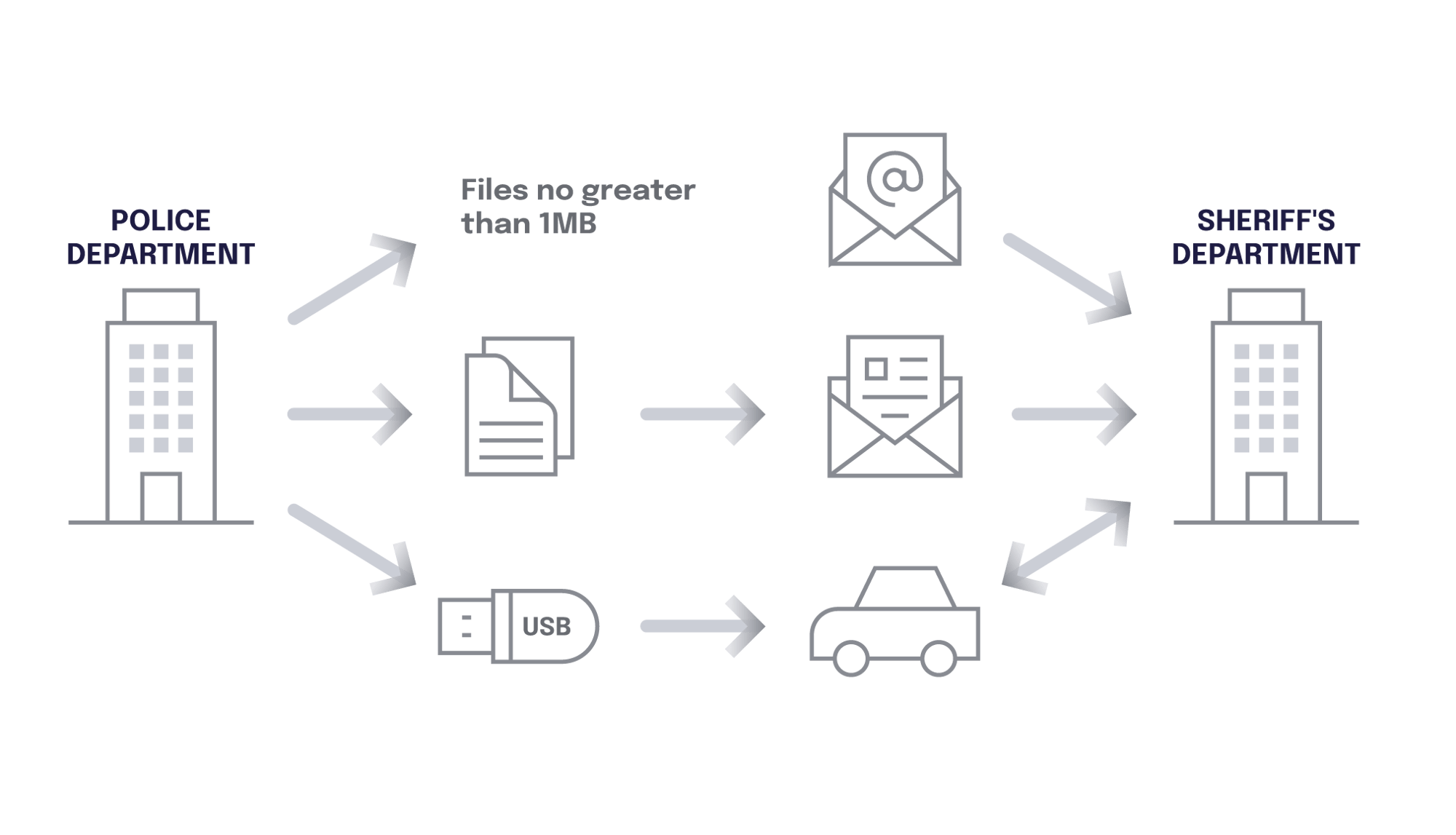
Your agency is still using USBs, hard drives or safe-hand couriers to transfer sensitive information between stakeholders.
![]()
Your agency uses encryption, but it is not end-to-end encrypted and it is complex and difficult for users to follow.
![]()
Your agency uses file-sharing technology that is not compliant and doesn't have fail-safe auditability and chain of custody.
![]()
Your agency doesn't have full control over who can access sensitive and confidential documents and data.
How secure are your current data sharing processes?
Vital questions you need to ask your team.

Share, store and collaborate in the cloud with totally secure file sharing for government and law enforcement
DekkoSecure's secure-by-design platform offers end-to-end military grade encryption. This means no unauthorized party can access your confidential and sensitive data.
Common risks:
Poor password management
Email attachment limits
No folders or permissions
Slow delivery
Theft, loss and interception
No verifiable audit trail
.png)
DekkoSecure:
Unlimited file size support
Fast upload & instant sharing
Easy 1-step registration
In-app content viewing
Secure workspaces
Comprehensive audit
Seamless, end-to-end encryption with Zero Knowledge
Who has unauthorized access to your sensitive files and discussions?
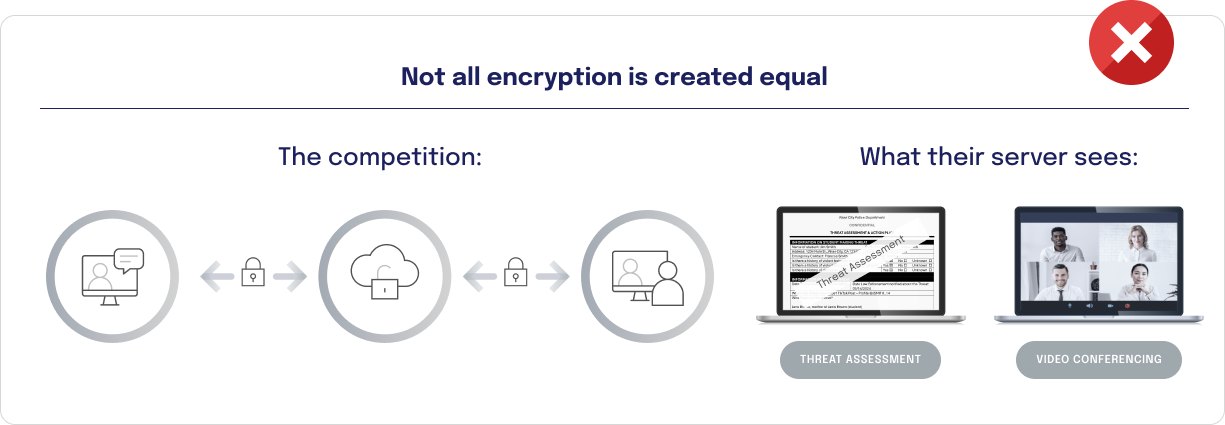
Keep your content safe from everyone - even DekkoSecure
Unlike competing platforms, all content exchanges take place on the end-to-end encrypted DekkoSecure platform with no reliance on third parties or add-ons.
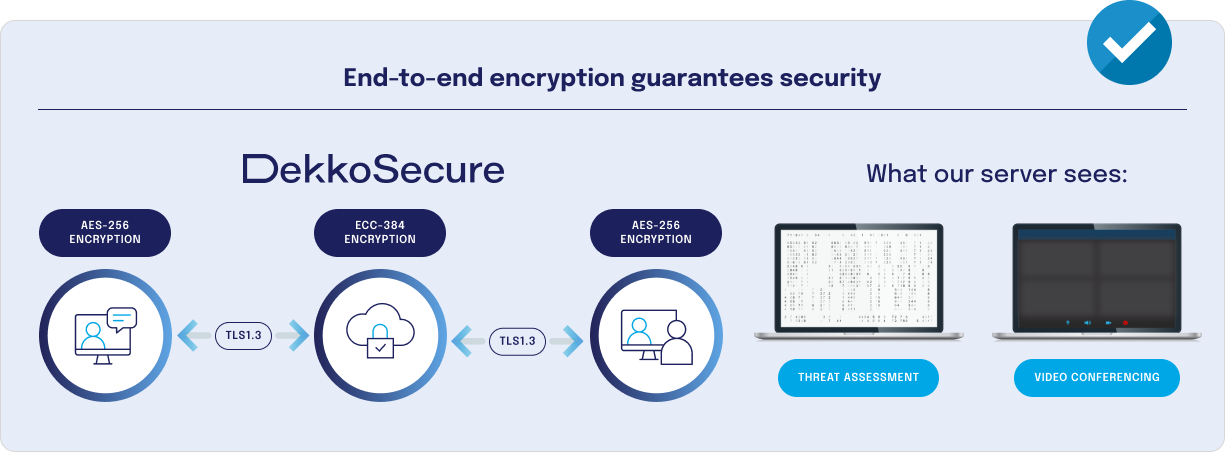
Zero Knowledge protocols are built into DekkoSecure’s collaboration features. Users’ private keys are protected and kept confidential by their password, so users can be confident that their information is protected from unauthorized access.
The DekkoSecure collaboration platform protects client information using end-to-end military grade encryption (E2EE). All content is encrypted on the sender's device and decrypted on the recipient’s device. Content is never accessible to an unauthorized third party (including DekkoSecure).
DekkoSecure is hosted on Microsoft Azure triple-redundant cloud in the US, which carries numerous compliance certifications such as ISO, CSA, SOC and IRAP-PROTECTED.
DekkoSecure helps organizations adopt the CIA triad
best-practice principles
The USA's National Institute of Standards and Technology has established best practices for data integrity, protecting assets against ransomware and other destructive events.
Those best practices include adopting solutions that consider the CIA triad representing the three pillars of information security: confidentiality, integrity, and availability.
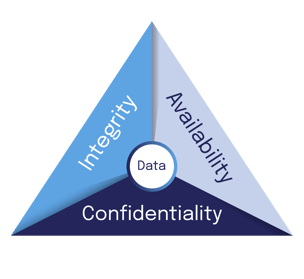
- Confidentiality - Preserving authorised restrictions on information access and disclosure, including means for protecting personal privacy and proprietary information.
- Integrity - Guarding against improper information modification or destruction and ensuring information non-repudiation and authenticity.
- Availability - Ensuring timely and reliable access to and use of information.
Five powerful tools on one secure platform
Protect your entire collaboration workflow with a single-minded approach to security.
Trusted by government and the most security-conscious organizations globally
Discover our totally secure file sharing for government and law enforcement
Talk to our team to learn more about the DekkoSecure platform and services or to discuss your agency's requirements.




