Experience real encryption in your browser!
This interactive encryption demo lets you see how secure message encryption actually works. Type a message, generate a unique key and watch the encrypted output transform instantly. Decrypt it again to confirm the process and get a clearer understanding of how modern cryptographic protection keeps information safe.
🔒 Everything runs locally; your text never leaves your device.
💡 To see how an incorrect key or content can affect decryption, change a character in the key or encrypted message.
Note: This tool is for demonstration only. For real-world secure workflows, use DekkoCORE for authenticated, end-to-end encrypted collaboration.
DekkoCORE is a more Efficient Way to Message Securely
When you need to discuss confidential information, manually encrypting messages and sending keys separately might feel secure. But imagine doing this with dozens of people, decrypting long email threads during high-stakes situations - all without central control, auditing or guaranteed recipient behaviour.
DekkoCORE solves these challenges by providing secure, end-to-end encrypted messaging built for real operational use.
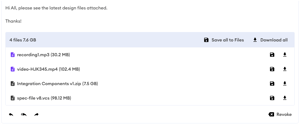
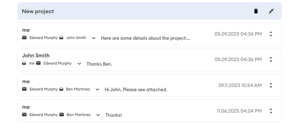
See DekkoSecure's Messaging Capability in Action:
DekkoCORE is built for the security and collaboration needs of agencies and organisations working with sensitive information, providing a secure and jurisdictionally controlled environment that keeps documents consistent, accessible, and trusted across every stakeholder.
Data Sovereignty
DekkoCORE is cloud-based, with data sovereignty options for Australia, Canada, the United States and Switzerland.
Compliance Status
DekkoCORE is:
IRAP assessed (PROTECTED)
DSPF Compliant (DISP)
GO-ITS/ITSG-33 aligned
CJIS Security Policy mapped
GDPR aligned
No file size limits
DekkoCORE supports files of any size or format, allowing your organisation to handle everything from routine documents to massive file collections with confidence.
Groups for Processes
DekkoCORE features flexible groups called "Hubs" that organise people, files, user visibility, and workflows, making it simple to control access and coordinate secure operational activity.
Ready to reach out?
If you’d like to learn more about DekkoSecure or discuss your requirements, our team is ready to assist.











